VAPT
Vulnerability Assessment Penetration Testing
What is Vulnerability Assessment & Penetration Testing (VAPT)?
Vulnerability Assessment and Penetration Testing (VAPT) are both security services that focus on identifying vulnerabilities in the network, server and system infrastructure. Both the services serves a different purpose and are carried out to achieve different but complimentary goals.
Vulnerability Assessment focuses on internal organizational security, while Penetration Testing focuses on external real-world risk.
How should we define the scope for a Vulnerability Assessment & Penetration Testing (VAPT)?
The scope for each audit depends on the specific company, industry, compliance standards, etc. However, the following are some general guidelines that you should consider:
- Any and all devices with an IP address can be considered for a VAPT activity.
- Penetration Testing should focus on your organizations external parameters (IP Addresses, Offices, People, etc)
- Vulnerability Assessment should focus on your internal infrastructure (servers, databases, switches, routers, desktops, firewalls, laptops, etc)
Do I need to conduct a Vulnerability Assessment & Penetration Testing (VAPT)?
Cyber attacks and threats are a real-world problem today with thousands of networks and websites and being compromised every day. Some of the normal reasons we see for carrying out a Vulnerability Assessment & Penetration Testing (VAPT) are as follows:
- Customer needs – It is becoming common practice today for customers to request Security Certifications from their partners or vendors.
- Compliance – A large number of industry standards & regulations have included Vulnerability Assessment & Penetration Testing (VAPT) as a mandatory requirement.
- Security validation – Vulnerability Assessment & Penetration Testing (VAPT) helps validate your security controls and measures against real-world attacks.
- Best-practice & data security – As attackers scale and threats evolve, there is a need within organizations to carry out proactive security audits to protect their data and systems from evolving threats.
Various VAPT Tests
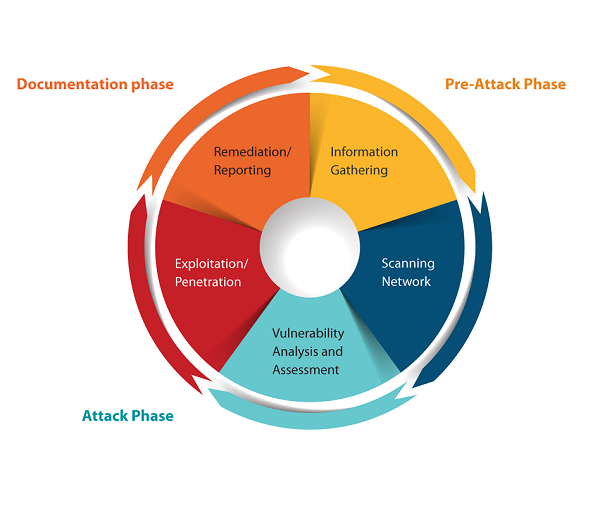
NETWORK PENETRATION TESTING
Infrastructure vulnerabilities are mainly instigate through poor configuration or inadequate patching policies or processes...
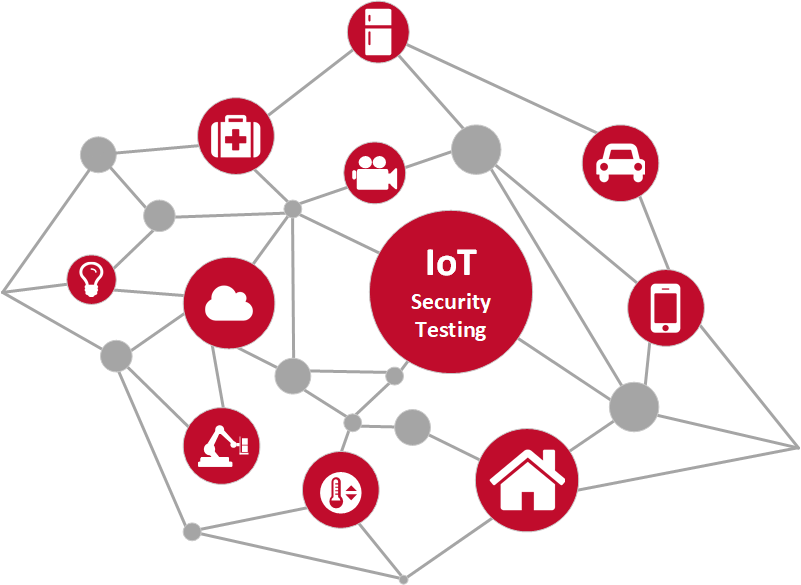
IOT PENETRATION TESTING
The IoT is a giant network of connected "things" (which also includes people). The relationship will be between people-people, people-things, and things-things...

CLOUD PENETRATION TESTING
Cloud security is essential to assess the security of your operating systems and applications running on cloud.Ensuring ongoing security in...

WEB APPLICATION PENETRATION TESTING
To evaluate the security of a system by methodically validating and verifying the effectiveness of application security controls...

WIRELESS PENETRATION TESTING
Wi-Fi technologies pose unique threats because their signals propagate outside physical boundaries and are difficult to control...

RED TEAMING
Red teaming activities comprises of different type of penetration testing including the physical data theft to test the defense capabilities of any organization...

MOBILE PENETRATION TESTING
Mobile penetration testing will identify any vulnerabilities within the mobile infrastructure of your business.A Mobile device assessment can be performed..
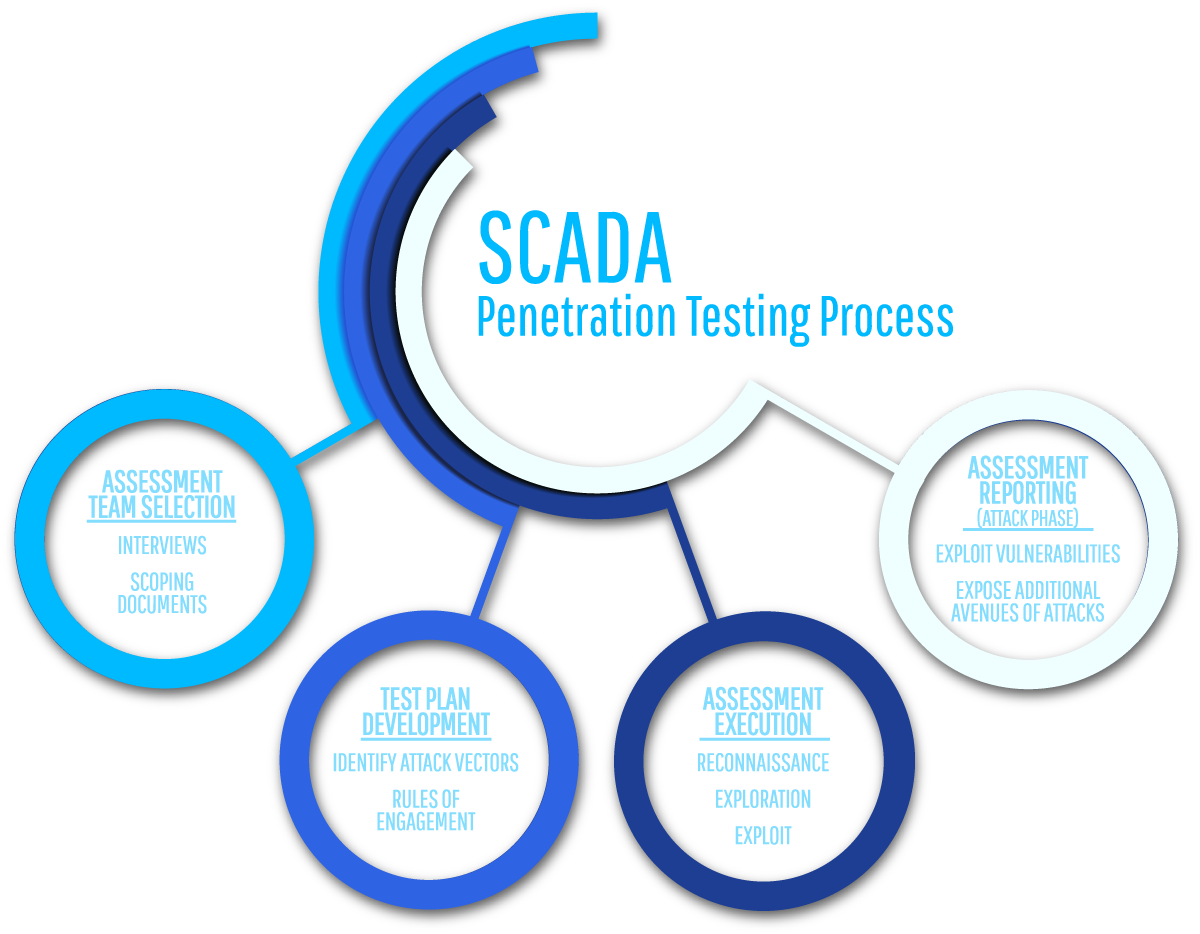
SCADA PENETRATION TESTING
SCADA stands for Supervisory Control and Data Acquisition. In very simple terms, SCADA defines a type of control system that is used to control and ...
Infrastructure vulnerabilities are mainly instigate through poor configuration or inadequate patching policies or processes. Our security assessments and tests attempt to exploit these vulnerabilities. Common targets of network and infrastructure attacks are over the network components including firewalls, routers, key servers or other devices or components that have an IP address that could be accessed.
- Hackers will often actively or passively scan networks for holes and vulnerabilities. Security analysis and vulnerability assessment professionals are key players in identifying potential holes and closing them off.
- Security analysis can help in identifying any vulnerabilities in a computer, network, or communications infrastructure, then each is prioritized and addressed with “protect, detect, and react” security plans.
- Penetration testing is carried out in various phases to ensure clear planning and delivery model.
- Information Gathering
- Threat Modeling
- Vulnerability Analysis
- Exploitation
- Post-Exploitation
- Reporting
- Our expertise covers all aspect of security and perform it in accordance to the most updated security frameworks like OWASP, NIST SP 800 115, OSSTMM, PTES, WASC and ZCTF.
- Our approach is based on the advanced manual test to ensure no false positives.
- All the findings are compiled in an easy to understand format and rated based on their criticality level
- Risk, Technical Impact and Business impact shall be determined based on the vulnerabilities detected.
- Implications of the findings will be explained in detail.
- All the findings are supported with the relevant screenshots and Video Evidences (wherever possible).
- COMPONENTS
- Scope
- Control Framework (ie: OWASP, PCI, PTES, OSSTMM)
- Timeline
- Executive Summary Narrative
- Technical Summary Narrative
- Report Summary Graphs
- Summary of Findings
- Findings (Description, Business Impact, Recommendation, Evidence, References, CVSS, Risk Rating Calculation)
- Methodology and Approach
- Risk Rating Factors
- Tools
The IoT is a giant network of connected "things" (which also includes people). The relationship will be between people-people, people-things, and things-things. With billions of devices being connected together, what can people do to make sure that their information stays secure? The IoT also opens up companies all over the world to more security threats. Then we have the issue of privacy and data sharing.
Depending on what industry you are in -
- Smart Home Automation
- Medical/Healthcare
- Industrial Control Systems
- Wearable
- Energy/Utility
- Energy/Utility
- Automotive
- Retail
- Enterprise IoT
A typical IoT penetration test (Attacker Simulated Exploitation) would involve the following components:
- Attack Surface Mapping
- Firmware reverse engineering and binary exploitation
- Hardware based exploitation
- Web, Mobile and Cloud vulnerabilities
- Radio security analysis
- PII data security analysis (optional)
- Report preparation
- Re-assessment
- Our expertise covers all aspect of security and perform it in accordance to the most updated security frameworks like OWASP, NIST SP 800 115, OSSTMM, PTES, WASC and ZCTF.
- Our approach is based on the advanced manual test to ensure no false positives.
- All the findings are compiled in an easy to understand format and rated based on their criticality level
- Risk, Technical Impact and Business impact shall be determined based on the vulnerabilities detected
- Implications of the findings will be explained in detail
- All the findings are supported with the relevant screenshots and Video Evidences (wherever possible)
Components
- Scope
- Control Framework (ie: OWASP, PCI, PTES, OSSTMM)
- Timeline
- Executive Summary Narrative
- Technical Summary Narrative
- Report Summary Graphs
- Summary of Findings
- Findings (Description, Business Impact, Recommendation, Evidence, References, CVSS, Risk Rating Calculation)
- Methodology and Approach
- Risk Rating Factors
- Tools
Cloud security is essential to assess the security of your operating systems and applications running on cloud. Ensuring ongoing security in the cloud requires not only equipping your cloud instances with defensive security controls, but also regularly assessing their ability to withstand the latest data breach threats
Many organizations think Cloud Security is Cloud Provider's responsibility. It’s the cloud provider's responsibility to secure the underlying infrastructure that supports the cloud. But it's your responsibility to ensure you secure anything that you put on the Cloud.
It's important for you to provide Customer data security, Platform security, Application Security, Access management, OS Security, Network Security, Encryption etc. Arridae cloud security assessments help you have holistic cloud security.
- Penetration testing is carried out in various phases to ensure clear planning and delivery model.
- Information Gathering, Planning and Analysis
- Vulnerability Detection
- Attack(s)/Privilege Escalation
- False Positive Analysis
- Post Assessment
- Reporting
- Our expertise covers all aspect of security and perform it in accordance to the most updated security frameworks like OWASP, NIST SP 800 115, OSSTMM, PTES, WASC and ZCTF.
- Our approach is based on the advanced manual test to ensure no false positives.
- All the findings are compiled in an easy to understand format and rated based on their criticality level
- Risk, Technical Impact and Business impact shall be determined based on the vulnerabilities detected
- Implications of the findings will be explained in detail
- All the findings are supported with the relevant screenshots and Video Evidences (wherever possible)
Components
- Scope
- Control Framework (ie: OWASP, PCI, PTES, OSSTMM)
- Timeline
- Executive Summary Narrative
- Technical Summary Narrative
- Report Summary Graphs
- Summary of Findings
- Findings (Description, Business Impact, Recommendation, Evidence, References, CVSS, Risk Rating Calculation)
- Methodology and Approach
- Risk Rating Factors
- Tools
To evaluate the security of a system by methodically validating and verifying the effectiveness of application security controls. The process involves an active analysis of the application for any weaknesses, technical flaws, or vulnerabilities and to protect them against various security threats that exploit vulnerabilities in an application’s code. Common targets for web application attacks are content management systems (e.g., WordPress), database administration tools (e.g., phpMyAdmin) and SaaS applications.
- Often, businesses with online presence especially the payment systems pose bigger risk for the businesses thereby gaining attention due to the uncovering of flaws in major retailers, banks and/or other online businesses.
- Demonstration of risks in this scenario is pretty realistic and has been gaining speed both from new attacker vectors and covering old risks perspective, thereby encouraging staff to tackle this issue before it spirals out to cause damage of reputation or any related implications at legal level.
- Penetration testing is carried out in various phases to ensure clear planning and delivery model.
- Information Gathering, Planning and Analysis
- Vulnerability Detection
- Attack(s)/Privilege Escalation
- False Positive Analysis
- Post Assessment
- Reporting
- Our expertise covers all aspect of security and perform it in accordance to the most updated security frameworks like OWASP, NIST SP 800 115, OSSTMM, PTES, WASC and ZCTF.
- Our approach is based on the advanced manual test to ensure no false positives.
- All the findings are compiled in an easy to understand format and rated based on their criticality level
- Risk, Technical Impact and Business impact shall be determined based on the vulnerabilities detected
- Implications of the findings will be explained in detail
- All the findings are supported with the relevant screenshots and Video Evidences (wherever possible)
Components
- Scope
- Control Framework (ie: OWASP, PCI, PTES, OSSTMM)
- Timeline
- Executive Summary Narrative
- Technical Summary Narrative
- Report Summary Graphs
- Summary of Findings
- Findings (Description, Business Impact, Recommendation, Evidence, References, CVSS, Risk Rating Calculation)
- Methodology and Approach
- Risk Rating Factors
- Tools
Wi-Fi technologies pose unique threats because their signals propagate outside physical boundaries and are difficult to control. Poorly configured systems and weak security protocols allow for unauthorized eavesdropping and easy access. Use a proven methodology and sophisticated testing tools that prevent information, systems and networks from being compromised by:
- Assessing your wireless environment
- Identifying vulnerabilities and errant configurations
- Validating existing controls
Prioritizing high risk findings and remediation techniques.
You may be unaware of loopholes in your processes such as logging and monitoring, and may be unaware of anonymous connection abuse of your guest wireless networks or corporate networks. Similarly, DoS attacks rendering networks offline, abuse of wireless network by employees for non-work related browsing or downloads, sensitive information theft (using wireless point of sale systems or similar implementation), network infections, are a few of the implications if wireless networks are left without secure setup in place.
We uses a proven methodology and sophisticated testing tools that prevent information, systems and networks from being compromised by:
- Assessing your wireless environment
- Identifying vulnerabilities and errant configurations
- Validating existing controls
Prioritizing high risk findings and remediation techniques.
- Our expertise covers all aspect of security and perform it in accordance to the most updated security frameworks like OWASP, NIST SP 800 115, OSSTMM, PTES, WASC and ZCTF.
- Our approach is based on the advanced manual test to ensure no false positives.
- All the findings are compiled in an easy to understand format and rated based on their criticality level
- Risk, Technical Impact and Business impact shall be determined based on the vulnerabilities detected
- Implications of the findings will be explained in detail
- All the findings are supported with the relevant screenshots and Video Evidences (wherever possible)
Components
- Scope
- Control Framework (ie: OWASP, PCI, PTES, OSSTMM)
- Timeline
- Executive Summary Narrative
- Technical Summary Narrative
- Report Summary Graphs
- Summary of Findings
- Findings (Description, Business Impact, Recommendation, Evidence, References, CVSS, Risk Rating Calculation)
- Methodology and Approach
- Risk Rating Factors
- Tools
Red teaming activities comprises of different type of penetration testing including the physical data theft to test the defense capabilities of any organization. The attack simulation carried out by our highly trained security consultants in an effort to achieve the assets related to the people, process and technology.
The objectives are:
- Identify physical, hardware, software and human vulnerabilities
- Obtain a more realistic understanding of risk for your organization
- Help address and fix all identified security weaknesses
Red team assessment experts have trained in a wide range of disciplines and hold certifications from the following respected cyber security organizations:
- CREST
- GIAC
- EC-Council
- ISACA
- (ISC)²
- Offensive Security
Red Team focus on giving your security team practical experience real cyber attacks. While avoiding business damaging tactics, these assessments use conventional and advanced attacker TTPs to target agreed-upon objectives. You define the attack objectives — usually worst-case business scenarios — and the Mandiant red team goes to work. The Mandiant red team goes through full attack lifecycle, from initial reconnaissance to mission completion.
- Phishing and social engineering
- Physical data theft
- Web and mobile application evaluation
- Wireless and internal network assessment.
- Our expertise covers all aspect of security and perform it in accordance to the most updated security frameworks like OWASP, NIST SP 800 115, OSSTMM, PTES, WASC and ZCTF.
- Our approach is based on the advanced manual test to ensure no false positives.
- All the findings are compiled in an easy to understand format and rated based on their criticality level
- Risk, Technical Impact and Business impact shall be determined based on the vulnerabilities detected
- Implications of the findings will be explained in detail
- All the findings are supported with the relevant screenshots and Video Evidences (wherever possible)
Components
- Scope
- Control Framework (ie: OWASP, PCI, PTES, OSSTMM)
- Timeline
- Executive Summary Narrative
- Technical Summary Narrative
- Report Summary Graphs
- Summary of Findings
- Findings (Description, Business Impact, Recommendation, Evidence, References, CVSS, Risk Rating Calculation)
- Methodology and Approach
- Risk Rating Factors
- Tools
Mobile penetration testing will identify any vulnerabilities within the mobile infrastructure of your business. A Mobile device assessment can be performed to an agreed scope to test your company’s mobile security position and provide recommendations for how to better secure the broad range of mobile devices in use. The service is available for windows, iOS, and android platform.
Mobile application security assessment is the must do exercise to get an assessment of your applications to keep malicious users away from your infrastructure. Similarly, internal web applications are necessary to avoid leakage of information, unauthorized access to data, or to avoid potential damage by introducing insecure code.
- Penetration testing is carried out in various phases to ensure clear planning and delivery model.
- Information Gathering, Planning and Analysis
- Vulnerability Detection
- Attack(s)/Privilege Escalation
- False Positive Analysis
- Post Assessment
- Reporting
- Our expertise covers all aspect of security and perform it in accordance to the most updated security frameworks like OWASP, NIST SP 800 115, OSSTMM, PTES, WASC and ZCTF.
- Our approach is based on the advanced manual test to ensure no false positives.
- All the findings are compiled in an easy to understand format and rated based on their criticality level
- Risk, Technical Impact and Business impact shall be determined based on the vulnerabilities detected
- Implications of the findings will be explained in detail
- All the findings are supported with the relevant screenshots and Video Evidences (wherever possible)
Components
- Scope
- Control Framework (ie: OWASP, PCI, PTES, OSSTMM)
- Timeline
- Executive Summary Narrative
- Technical Summary Narrative
- Report Summary Graphs
- Summary of Findings
- Findings (Description, Business Impact, Recommendation, Evidence, References, CVSS, Risk Rating Calculation)
- Methodology and Approach
- Risk Rating Factors
- Tools
SCADA stands for Supervisory Control and Data Acquisition. In very simple terms, SCADA defines a type of control system that is used to control and monitor facilities and industrial infrastructure. Organizations use SCADA systems to automate complex industrial processes, detect and correct problems, and measure trends over time. SCADA systems are used in industries such as water management, building and facility management, traffic management, electric power generation, etc.
Over recent years, SCADA systems have moved from proprietary, closed networks and systems to open systems and TCP/IP networks. This has exposed these networks to the same risks that traditional computer networks face. However, this does not necessarily mean that the approach for security assessment remains the same for SCADA assessments.
- Penetration testing is carried out in various phases to ensure clear planning and delivery model.
- Information Gathering
- Threat Modeling
- Vulnerability Analysis
- Exploitation
- Post-Exploitation
- Reporting
- Our expertise covers all aspect of security and perform it in accordance to the most updated security frameworks like OWASP, NIST SP 800 115, OSSTMM, PTES, WASC and ZCTF.
- Our approach is based on the advanced manual test to ensure no false positives.
- All the findings are compiled in an easy to understand format and rated based on their criticality level
- Risk, Technical Impact and Business impact shall be determined based on the vulnerabilities detected
- Implications of the findings will be explained in detail
- All the findings are supported with the relevant screenshots and Video Evidences (wherever possible)
Components
- Scope
- Control Framework (ie: OWASP, PCI, PTES, OSSTMM)
- Timeline
- Executive Summary Narrative
- Technical Summary Narrative
- Report Summary Graphs
- Summary of Findings
- Findings (Description, Business Impact, Recommendation, Evidence, References, CVSS, Risk Rating Calculation)
- Methodology and Approach
- Risk Rating Factors
- Tools
